A New type of phishing
File archiver in the browser
A new phishing technique called "file archiver in the
browser" can be leveraged to "emulate" a file archiver software
in a web browser when a victim visits a .ZIP domain
Earlier this
month, Google began offering the
ability to register ZIP TLD domains, such as bleepingcomputer.zip, for hosting
websites or email addresses
the TLD's release,
there has been quite a bit of debate over whether they are a mistake and could
pose a cybersecurity risk to users
Threat actors, in a nutshell, could create a
realistic-looking phishing landing page using
HTML and CSS that mimics legitimate file archive software, and host it on a
.zip domain, thus elevating social
engineering campaigns
While some experts
believe the fears are overblown, the main concern is that some sites will
automatically turn a string that ends with '.zip,' like setup.zip, into a
clickable link that could be used for malware delivery or phishing attacks.
For example, if you
send someone instructions on downloading a file called setup.zip, Twitter will
automatically turn setup.zip into a link, making people think they should click
on it to download the file.
When you click on
that link, your browser will attempt to open the https://setup.zip site, which
could redirect you to another site, show an HTML page, or prompt you to
download a file.
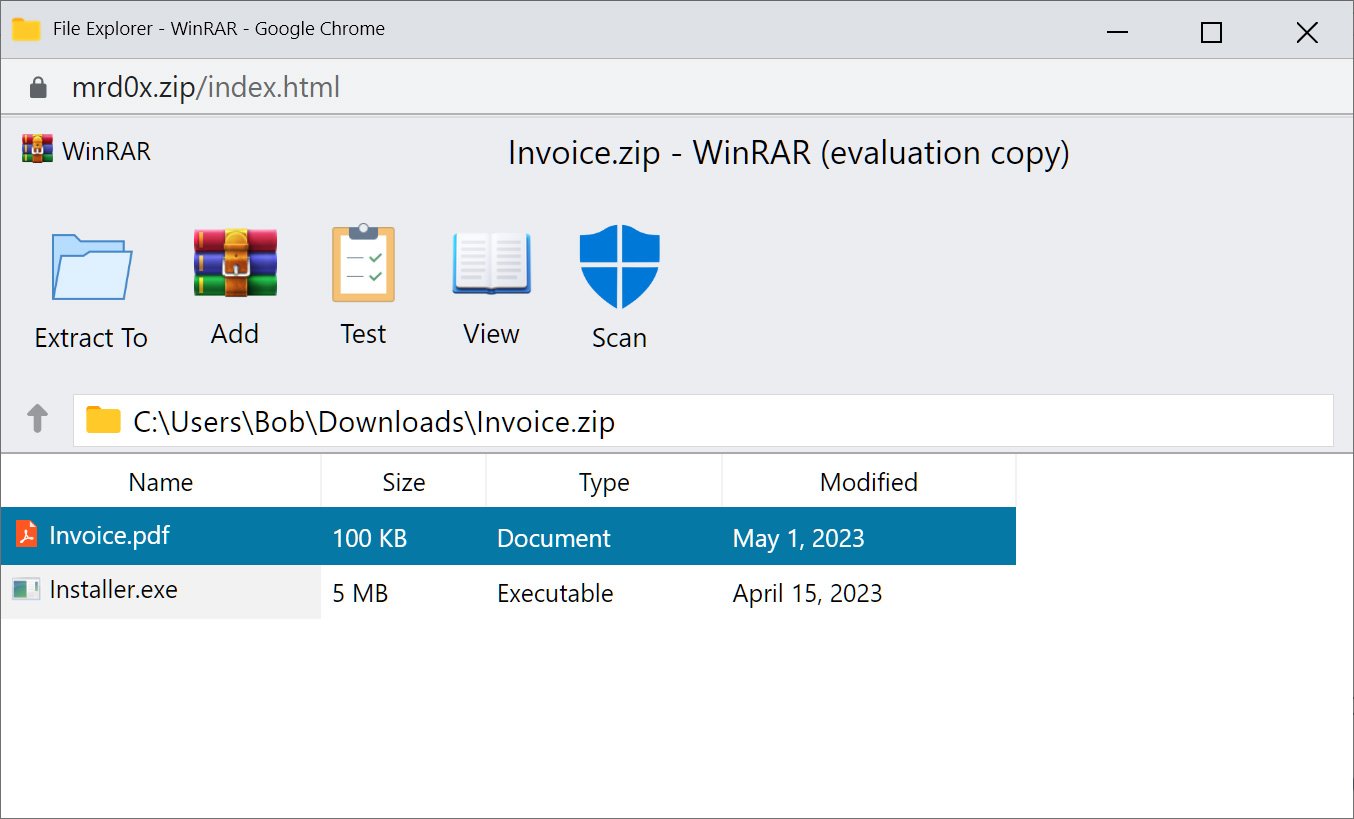
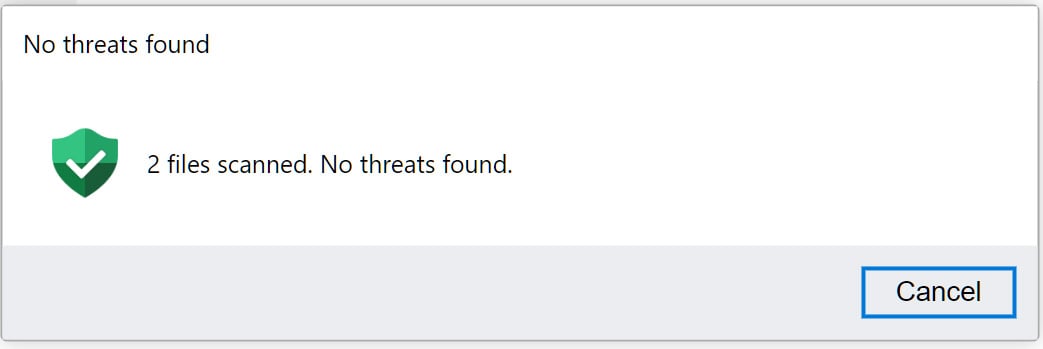
To make the fake WinRar window even more convincing, the researchers implemented a fake security Scan button that, when clicked, says that the files were scanned and no threats were detected







Comments
Post a Comment